TYPO3 Security Optimizations
According to the BSI security study on various CMS (Content Management Systems), TYPO3 doesn't score badly, and above all the infrastructure around TYPO3, with security bulletins, TYPO3 Security Guidelines and an official and very active security team, receives great praise.
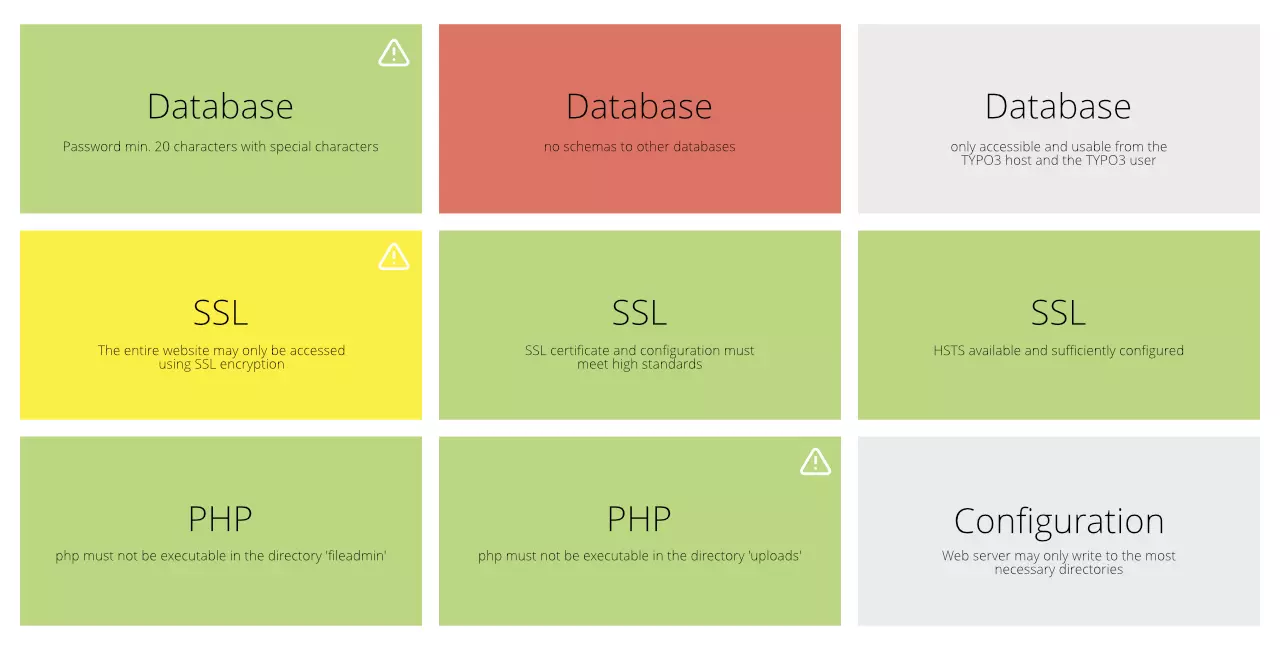
However, the system can be further optimised and secured by various measures. We particularly recommend the use of the Helmut Hummel Secure Web Package for further security. With this, PHP can only be executed in a few, defined places via Apache, which makes hacks via web shells almost impossible. Furthermore, HTTP Secure Headers and Cookie Domains should be configured so that the execution of foreign scripts is blocked. Also make sure to assign user rights as recessive as possible. Do all editors really need to be able to set HTML and iFrame content elements in TYPO3? In order to further protect the live system, tools such as the Content Publisher for TYPO3 can be used to completely do without editor users on the live TYPO3.
In addition, we recommend continuous monitoring of the TYPO3 core and any additional extensions used, including checking for security updates. Here, the use of a Caretaker server together with the Caretaker Extension for TYPO3 is recommended. On server level, tools such as ICINGA or Sentry should also be used.